Managing your cyber risk through education, leadership, and expert analysis.
Cybersecurity is more than IT doing its best to protect your data – it involves your entire culture. This is the most important thing executives and business owners need to know about cybersecurity.
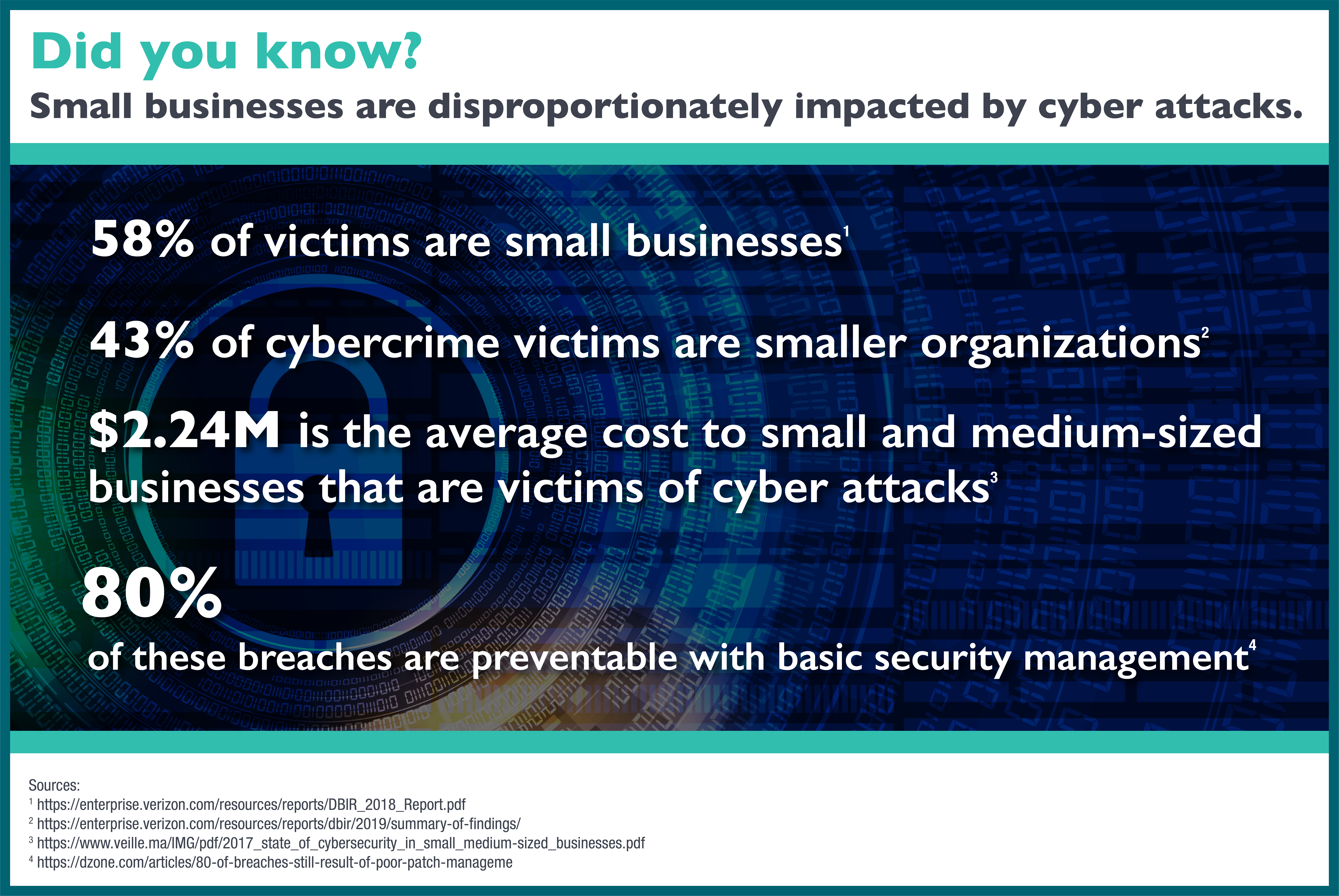
An organization’s information systems contain sensitive operational, business, and personal information which it must protect; this includes information about the organization, its staff, customers, and more.
Successful executives seeking to lead their organization to become cybersecure already possess the management acumen and leadership passion required to manage cyber risk. What’s most often missing is domain specific knowledge and expertise.
We can help you protect against:
- Cyber Fraud
- Business email compromise
- Information theft
- Ransomware
- Denial of service attack
- Regulatory compliance
- Disaster
And keep you compliant with:
- HIPAA HITECH
- Gramm-Leach-Bliley
- Payment Card Industry Data Security Standard
- California Consumer Privacy Act (CCPA)
- The European Union GDPR and other state privacy laws
- New York Financial Cybersecurity Regulations (23 NYCRR 500)
- Breach Disclosure laws
Our expertise lies, in part, in knowing how to apply best practices to the specific operational needs of individual organizations.
- NIST Cybersecurity Framework
- ISO 27001-02
- The Center for Internet Security CIS-20 Controls
- NIST 800-171
Cybersecurity is not a problem to solve; it's a situation to manage.
The Information Peace of Mind Program is a comprehensive starting point for implementing an organization’s Information Security Management Program and appointing a Virtual Chief Information Security Officer (vCISO) for ongoing management of the program.

Throughout the process, we identify IT security management weaknesses and current security vulnerabilities in your IT network and provide prioritized, specific management and technical recommendations for improving your information security management capabilities.
The program is designed to provide commercially reasonable security, be integrated into the organization’s culture, use staff and executive time efficiently, and be flexible to fit the differing needs, responsibilities, resources, and cash-flow of each organization.

We brief the organization’s executive leadership and IT management on the fundamental strategic imperatives required to meet today’s cybersecurity challenges.

We provide the organization a perpetual-use, non-exclusive license to our Information Security Policies and Standards to establish an information management structure and set basic information security expectations across the organization.

We conduct a story-filled, 100-minute Information Security Awareness Training workshop with management and staff – designed to illustrate the relevance, importance, and consequences of information security management.

We conduct a simulated phishing attack on your organization; staff who take the bait and click the link are directed to a landing page where they receive phishing defense training. Management gets a report identifying all staff who clicked on the link.

We meet with your team to review its preparation for responding to a security incident (e.g., ransomware attack) or a business disruption (e.g., earthquake). We review the preparation of plans, hosting backups, management of critical documentation, ability to respond, and training – both inside and outside of IT.




